Short version:
In 2013, Google released a tool to view the manual actions (penalties) they were applying to your own site. I discovered the API endpoint did no authorisation checks, and thus I had access to the full manual actions database.
I reported the issue to Google, who took the tool down for a couple of days to fix it, and paid me a $5000 bug bounty reward. Google didn’t block me from writing a blog post at the time, but I didn’t think they were going to be happy about it, so I’ve waited until now (10 years later!) to write this up.
August 9th 2013 was a Friday. I remember being at work and hearing that the evening before Google had released a viewer for manual actions. Before this, as crazy as it may seem nowadays, you simply didn’t know if Google were penalising you or not.
So the tool was a big deal, and the SEO agency I worked at were very interested in reviewing all our customers’ reports (all good!). We were able to access these reports as we had access to these customers’ Google Webmaster Tools (as it was then called) accounts.
I decided to inspect (on my own time) the API calls behind the scenes. I initially checked if it leaked additional info about penalties – it didn’t.
So I then decided to sanity check that I couldn’t access reports for sites that I shouldn’t have access to.
The payload that went to the API looked like this:
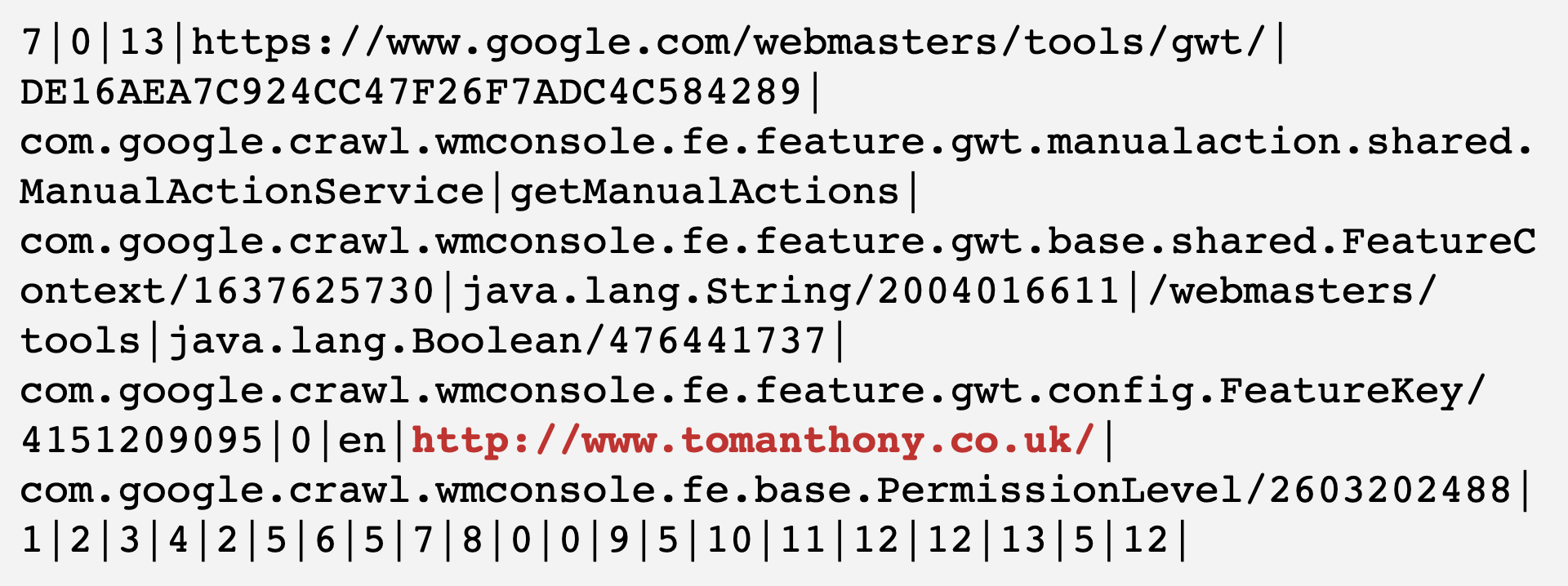
I’ve highlighted the obviously interesting part. Utilising my elite level hacking 😉 skills I replayed the request but updated the it to look like this:
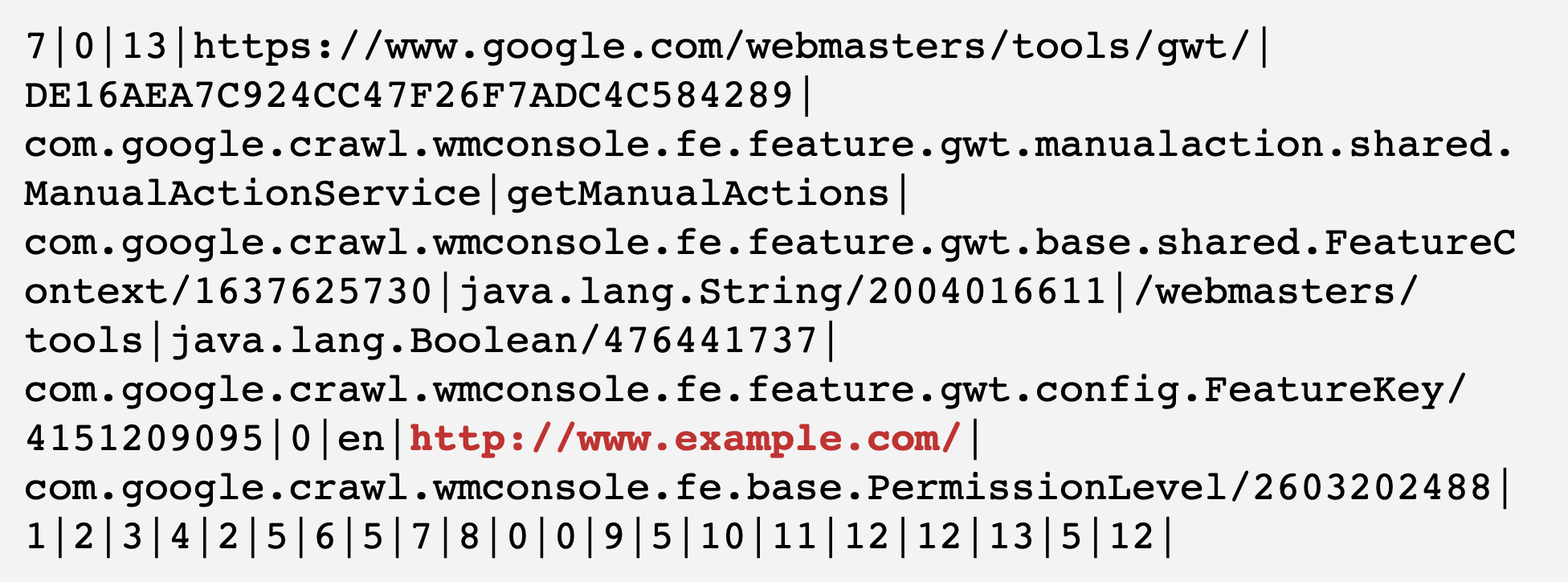
Shockingly — IT WORKED. I could put any domain name there and I could view the penalties associated with that domain. It appeared there was no authorisation being done at all — a serious and surprising oversight by Google.
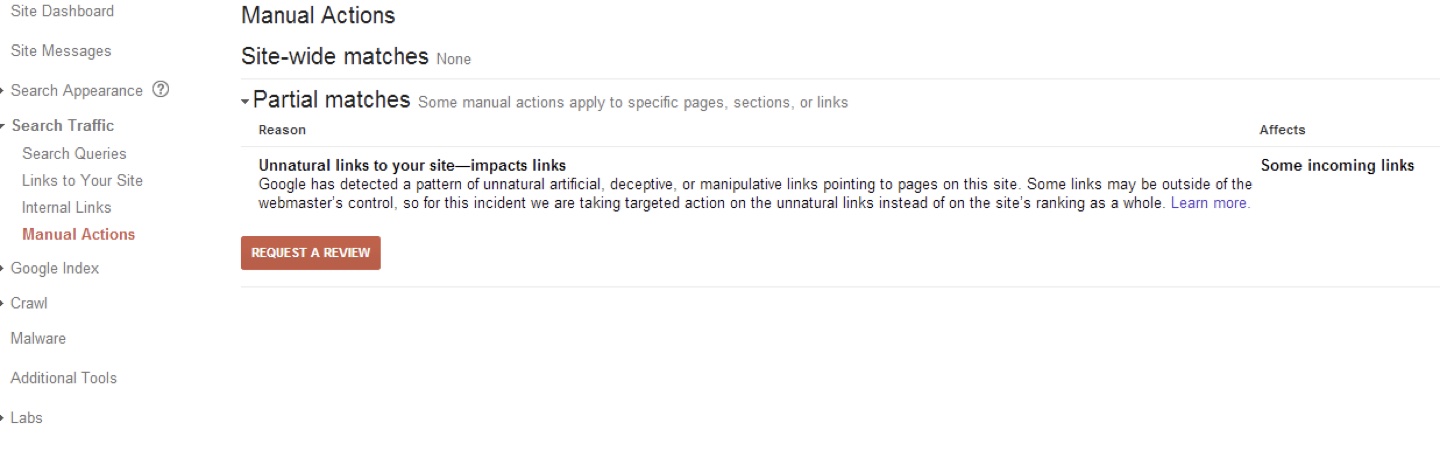
In the hands of a black-hat SEO, these were the key to the castle, as you could now target negative SEO attacks at your competitors to amplify existing penalties they had. It would have been very difficult for victims of such a targeted attack to recover.
I immediately reported the issue to Google. I reported it to both their bug bounty program (my introduction to bug bounty), and I emailed the infamous Matt Cutts (who replied in less than 15 minutes and was very grateful and very nice about the whole thing). Within a few hours they had pulled the tool down, blaming a ‘snag’:
It came back online after the weekend, but without any explanation of why it had been taken down. I have since spoken about this at conferences, but never written about it publicly.
Google paid me $5000 under their bug bounty program, and thus I was introduced to the world of bug bounties. I went on to hack Google’s core search functionality, and found Zoom didn’t rate limit their numeric meeting passwords in my efforts to join Boris Johnson’s cabinet meeting.
Thanks for reading! You can follow me on Twitter here: @TomAnthonySEO.
